Zemana AntiMalware user manual
Zemana AntiMalware user manual
This is a short guide, which will help you to install and use Zemana AntiMalware properly. The guide is created to be as easy as possible so that everyone could use the program by themselves.

Before using the software, make sure that your operating system is on this list: Windows XP (Service pack 2 or higher), Vista, 7, 8, 8.1, 10. Both 64 & 32 bit systems are supported. You can also get the mobile version, which is created for Android.
Zemana AntiMalware download
The first thing you need to do in order to use the software is downloading it. The installation file is very small and the downloading process should be completed in a few seconds.
Zemana AntiMalware installation
The installation process is simple and you will be able to install the app in a few minutes from now. To begin, open the file that you downloaded and follow the further steps.
1. This is the installation window. Close all the other applications if possible to be sure that the installation will be successful. After that, click “Next”.
2. This is the license agreement window. It is recommended to read the information so that you would know what terms you are accepting. Choose “I accept the agreement” if you accept it and click “Next” to proceed.
3. This is the location where the Zemana software is going to be installed. You can just leave the default location or change it and proceed by clicking “Next”.
4. There you can choose which options you would like to add. We recommend you to choose both of them because a desktop icon will let you reach the program as fast as possible, and the Real Time Protection is one of the most important AntiMalware features. Click “Next” to begin the installation.
You have finally completed the installation of the anti-malware program. It will open automatically after you install it.
Main features
There are not many features in this software, but all of them are the most important and necessary for the best protection results. The most important features can be reached via the main screen.
You can drag and drop suspicious folders right on the main menu so that Zemana AntiMalware could deeply scan them.
Scan – this is the feature, which will be used the most. It will perform a full scan of your computer. Do not expect to see a quick scan. There is no such feature because most of these scans are useless and only a deep scan can find the most threats.
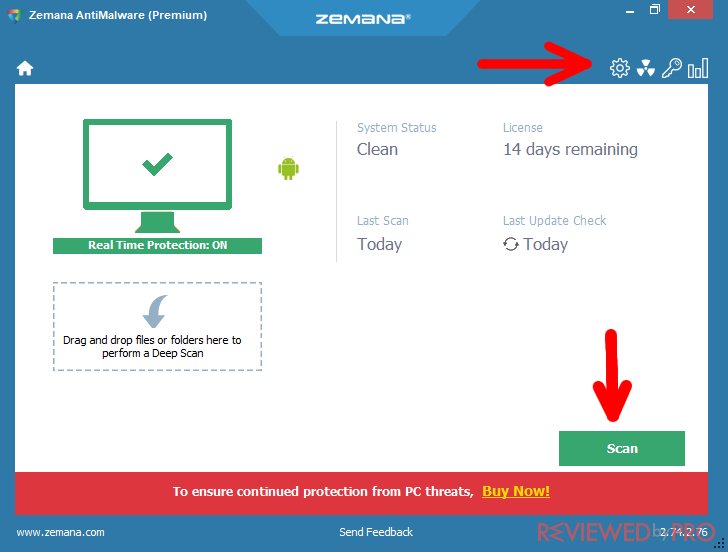
There is a menu at the top right corner too, composed of four icons. You can choose from four sections here:
Settings – you can manage the whole software in this section. These settings include the general, scan, exclusions, and other sections.
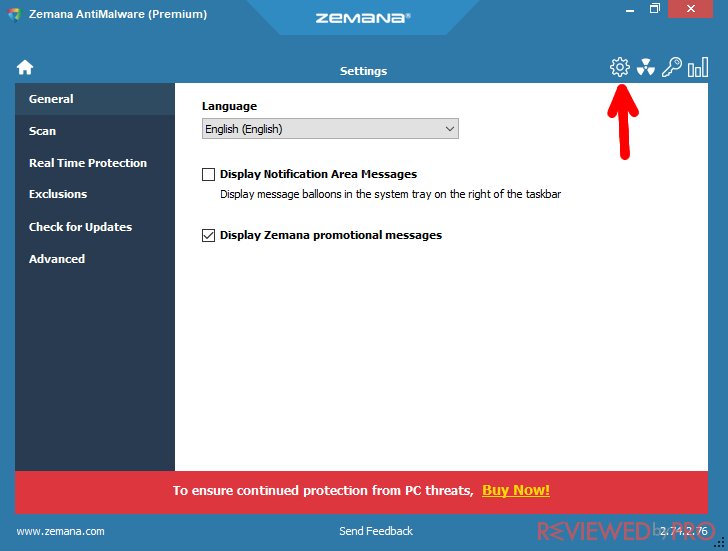
Quarantine – there will be a list of quarantined files, which were found in previous scans and quarantined by you. As they are harmless here, you can choose what to do with them whenever you want.
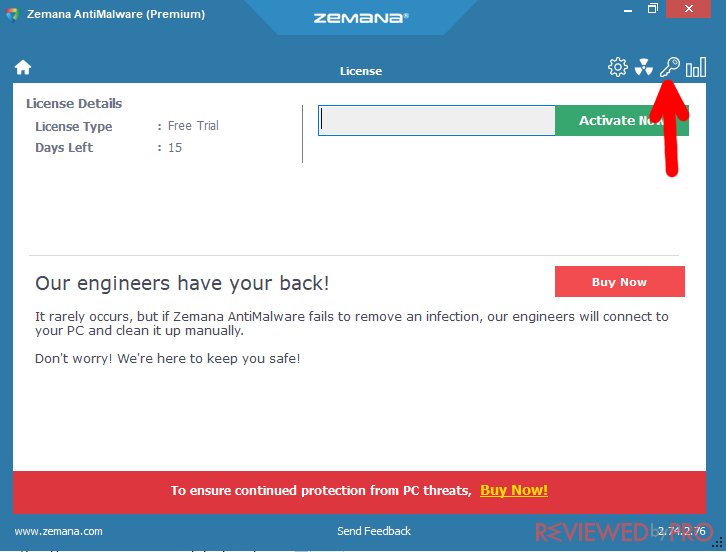
License – this is the activation section. You can activate or buy the activation code here.
Reports – this table contains all the information about previous scans.
The interface is not usual, but it is very simple as soon as you get used to it.
Scanning with Zemana AntiMalware
Performing a scan with Zemana AntiMalware is very easy. You only need to open the program, click on “Scan”, and a full scan will begin immediately.
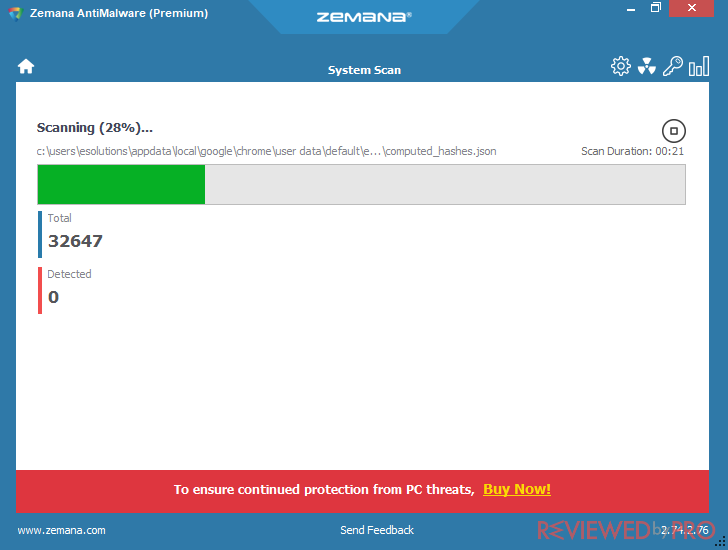
It will take some time to complete. If your PC has infected files, they will be shown after the process is completed and you can choose what to do with them – delete, quarantine, exclude and more.
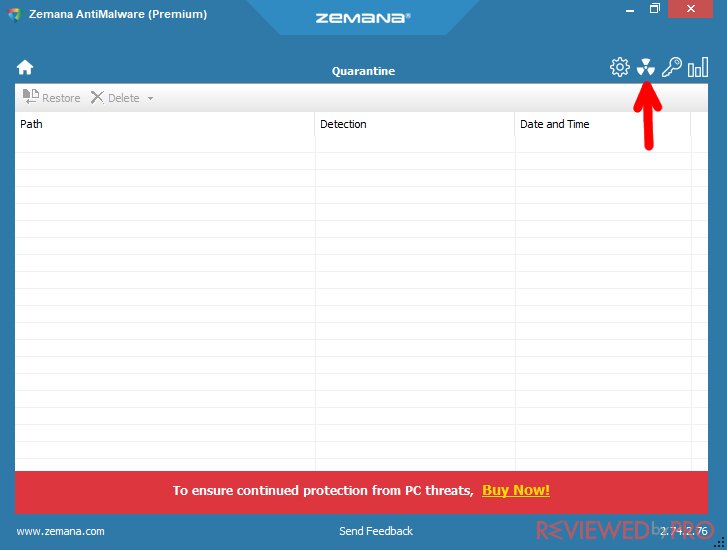
If you choose to quarantine infected files, do not forget to check the Quarantine section to decide what to do with these threats.
Getting the full version
You can try getting the full version of Zemana from this website. You will have to fill in the billing information. Click “Place Order” after you fill in all required fields.
And that is all, you have successfully bought the full version of Zemana AntiMalware software!




