Two-factor authentication could the most effective way to protect your accounts. However, authentication methods such as SMS messages became vulnerable to cybercriminals. This article will reveal the most commonly used authentication methods and evaluate their security.

When it comes to two-factor authentication, also known as 2FA, it includes a variety of forms including SMS message codes, email code, authenticator apps for your smartphone, or a hardware key. It is important to understand that using any method of 2FA is better than not having one, so do not disable 2FA just try to avoid using SMS.
The National Institute of Standards and Technology revealed the study that introduces 2FA. The study revealed that SMS is an old protocol with potential security flaws and vulnerabilities. As a result, more secured methods should be used. Even though businesses are not forced to follow National Institute of Standards and Technology’s recommendations, it is expected that companies will avoid SMS method over time. So if you are using SMS, you should consider switching to something else.
Authenticator applications such as Authy and Google Authenticator even though are more difficult to set up, they are much safer
The main idea of 2FA is to apply something the user knows (a password) and something the user has, for example, a phone, or any other device. Authentication applications, such as Authy,[1] turn the phone into that something user has without involving anyone else.
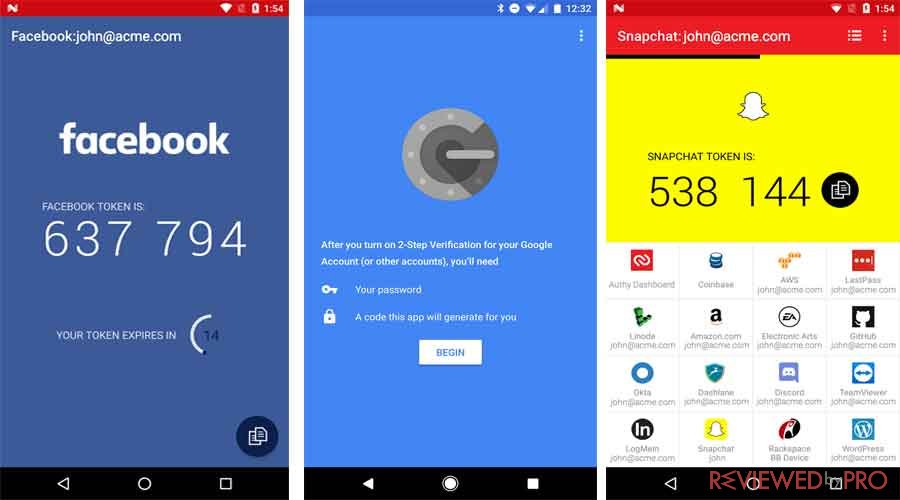
When the user sets Authy up, an account creates a secured seed key which shares it with your device through a QR code. The seed is encrypted on both ends and applies present time in order to generate a new code every half a minute. Only user and the server know the seed, so a criminal or hacker is not able to predict what the next authentication code could be.
Authentication applications have a lot of advantages over the SMS or email method. For beginners, the user is the only one aside from the server itself which can generate codes without involving email provider, cell carrier, or any other third-party. The codes are generated on the user’s device and only the user transfers them during the 30-second brief. So even if a cybercriminal would be able to intercept the message, it would not be of any use.
A vast majority of major services such as Dropbox, Amazon, Evernote and LastPass support authentication applications and the trend is still rising. However, these mentioned applications still include some risks. Third-party applications such as Authy enables users to sync the seed tokens across multiple devices. This could possibly open up a hacker to swipe a device the user does not look at or loses control of. In addition, a hacker could potentially hack the authentication service itself and get access to user’s seed keys. So, if someone breaks in, they are likely to get useful information.
However, it is worth mentioning that technically authenticators are the safest to use, and the least likely to being hacked or compromised if the device gets lost, or if the user forgets the password.
One-Button Authentication. Easier and simpler to use and to set up, however, most devices do not support it
The most recent 2FA method is one-button authentication. One-button authentication[2] works similar to the authentication application mentioned before, only the user does not need to manually copy a six-digit code from the user’s device to a text box. The user only needs to tap Yes, that is me and he is able to go. Google and Blizzard use this 2FA method.
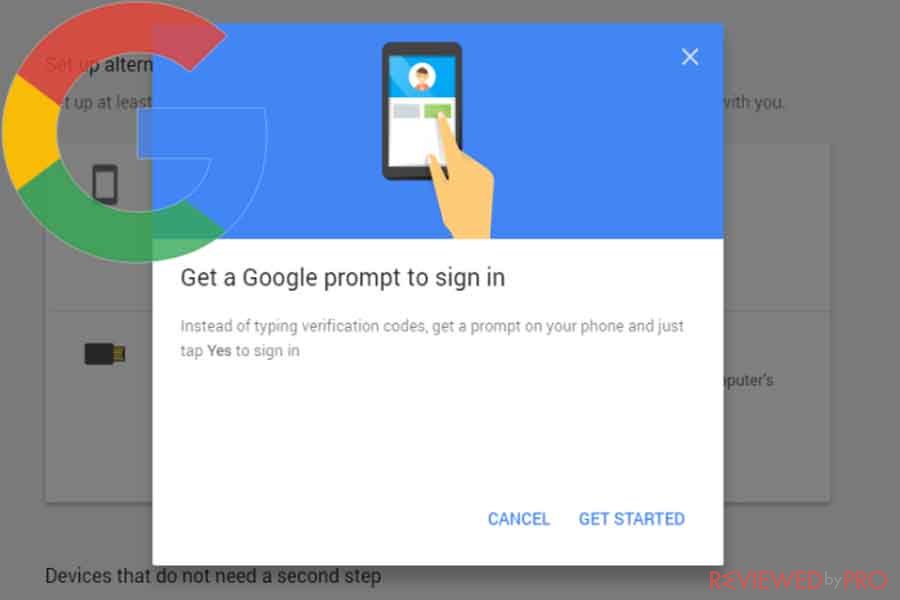
The main difference between one-button authentication and authentication applications is that the user does not have to enter the codes manually. Blizzard will display for the user a code on one of the user’s devices and will ask if that matches the one on the other device. Meanwhile, Google does not show any code at all, but users can expect that if they are not trying to log into the account, they should turn it down.
The one-button authentication method is likely to be as secure as generated codes in authentication applications, but it is new and most devices do not support it. So if you prefer to create your logins in a simpler way, you can trust this method.
Emailed codes. Slightly safer than SMS messages, but cannot be controlled
Some of these services enable users to confirm the logins through email. This way is actually safer than SMS codes but has some weaknesses too. For beginners, the email provider is a weak element. If someone can access to user’s email account, they also can get 2FA codes. Some of the companies, including Google protects your security pretty well, it still adds potential flaws.[3]
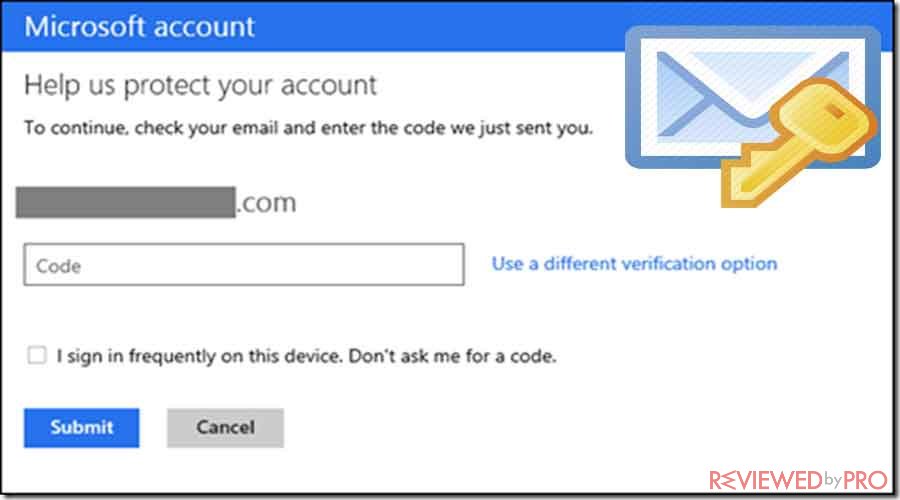 In addition, email can suffer from user-generated issues just like SMS codes. For instance, many users’ devices and applications have access to their email account, as well as third-party services can have access to these emails. So a hacker can swipe any of your devices or break into an old contacts application or calendar, which also can have access to email and log into your accounts before you even realize it.
In addition, email can suffer from user-generated issues just like SMS codes. For instance, many users’ devices and applications have access to their email account, as well as third-party services can have access to these emails. So a hacker can swipe any of your devices or break into an old contacts application or calendar, which also can have access to email and log into your accounts before you even realize it.
However, email is still more secure than SMS. The majority of email providers encrypt users’ massagers while in transit. But it is worth to mention that cybercriminals are able to get access to users’ email by attacking the email provider, third-parties or by using one of the users’ devices. So even though email is slightly more secured than SMS, if you have an option to use something else, you should try it.
SMS codes are everywhere but not secured
SMS codes provide users easy access but it is not a secure method of 2AF. 2AF assumes that users get the codes on a phone that only they control, hoverer, SMS are not able to guarantee this. Cybercriminals are able to potentially intercept SMS messages on their way to potential victim’s phone, or simply clone SIM card and get access to all of the potential victim’s accounts. In addition, carriers are included too, so there is a possibility that someone could try to convince them to transfer the victim’s phone number to another device. So, even though these ways are pretty difficult, they are much easier than breaking other 2AF forms.
Authentication apps, one-button authentication, email, and SMS are not only methods available. There are also phone calls or hardware keys. Phone calls suffer similar risks such as SMS messages, and hardware keys are not that popular. When it comes to security, there is no a completely secured and perfect solution but some methods are better than others.
- ^ Authy. Authy.
- ^ LastPass Authenticator Now Has a One-Button Approval Option. LifeHacker.
- ^ Two-Factor Authentication: Who Has It and How to Set It Up. PC Magazine.




